Cameyo protects its own instances from HTTP and RDP-related threats by using a unique, zero-maintenance security functionality.
As soon as you enable Remote functionality on a Windows machine, you effectively open its RDP ports to the outside world, specifically ports 3389, 3387, 3392. Hence, if your server is directly connected to the Internet, you are vulnerable to RDP brute-force and vulnerability attacks. According to our own study, a Windows device directly connected to the Internet is prone to hundreds of thousands of password attempts every week, performed by automated bots, scripts, viruses and zombie machines. RDP exploits are also part of the equation, with vulnerabilities such as BlueKeep.
Cameyo's RDP Port Shield feature is a unique, dynamic firewall feature which addresses this threat by closing RDP ports at the Windows Firewall level, and then opening them specifically to authenticated users if / when needed. It works by creating and managing in real-time an RDP white-list firewall rule on the server.
Activation
Port Shield functionality can be configured in your Cameyo's server page. It is enabled by default:

You can add a list of comma-separated IP addresses that always need to be allowed through. In most cases this is not necessary, as even administrative access is dynamically allowed when needed, as explained below. Changing this setting requires a service restart. This can be done using the "Restart service" button.
Under the hood
Port Shield mechanism works in 3 phases:
1.Upon service start, Cameyo disables any existing Windows Firewall rules that allow access to HTTP/RDP ports. It then adds its own white-list rules named "Cameyo Port Shield (TCP/UDP-In)". If any white-listed "admin IPs" rules were specified in Cameyo's configuration (see above), these are added as pre-authorized addresses; otherwise a placeholder address "255.255.255.254" is added instead. At this point, no HTTP/RDP access is allowed to the machine.
2.When approved Cameyo sessions are initiated through the Cameyo portal (i.e. online.cameyo.com/apps/xxxxx/play), one of two scenarios take place:
a.When regular HTML5 sessions are started, no changes are made. HTTP/RDP ports remain closed. Cameyo's HTML5 sessions do not require user-to-server HTTP/RDP port interaction.
b.When direct RDP sessions are started, Cameyo's portal (through which users authenticate to initiate sessions) informs the relevant server to open RDP access to the requesting user's IP address. Direct RDP sessions include: Admin access (i.e. through Cameyo portal's "Generate .RDP file" button), sessions initiated using Cameyo's Native Player, or sessions initiated through mobile Android devices.
3.White-listed IP addresses are removed and cleaned up upon Cameyo service restart, typically every few hours.
Example workflow
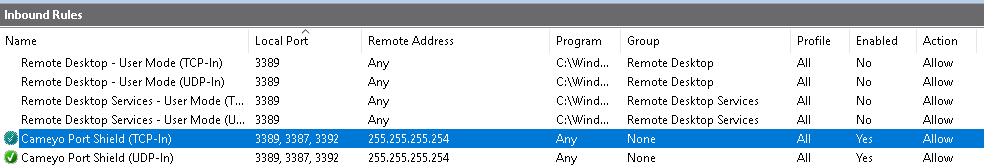
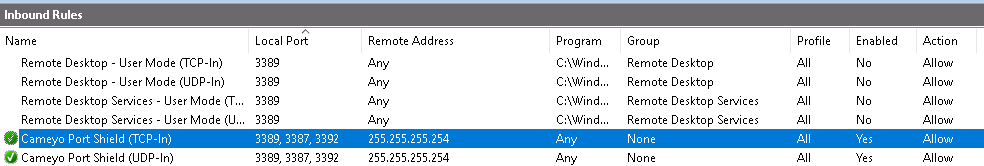
In the below example, Cameyo's Port Shield has disabled built-in RDP allow rules. It added its own rule with placeholder 255.255.255.254 address.
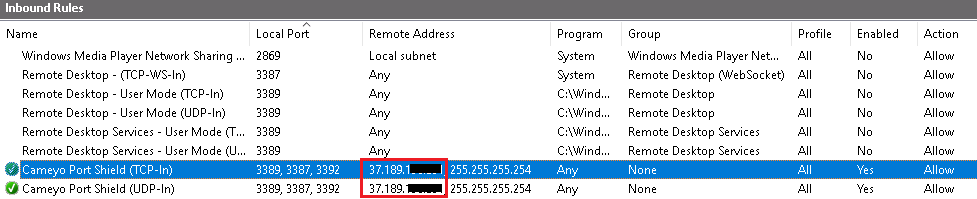
Following a portal-authenticated direct RDP session request, Port Shield has added authorization for the RDP connections coming from the 37.189.xxx.xxx address:
This access permission will be cleared up upon the next Cameyo service restart within a few hours, bring it back to pre-white-listed IP addresses only: